Cyber security can mean both the practice and the steps that are taken to keep electronic data safe from fraud or unauthorised use.
Cybersecurity’s main goal is to keep electronic data safe from people who aren’t supposed to use it or who are breaking the law. To keep data safe and stop bad people from accessing or compromising it, different rules and procedures need to be put in place.
As cyber threats become more common, it is important to know the different kinds of cyber security services that are out there to protect yourself.
What Are the 6 Areas of Cyber Security?
Check Point says that cybersecurity is all of the things that a company does to keep its employees and property safe from cyber threats.
As cyberattacks get more common and smarter and as corporate networks get more complicated, companies need a wider range of cyber security options to lower their cyber risk. You can find more information about the different kinds of cyber attacks in our post about them, in case this is something that worries you.
There are at least six areas that are often talked about when we talk about cyber security services. These are
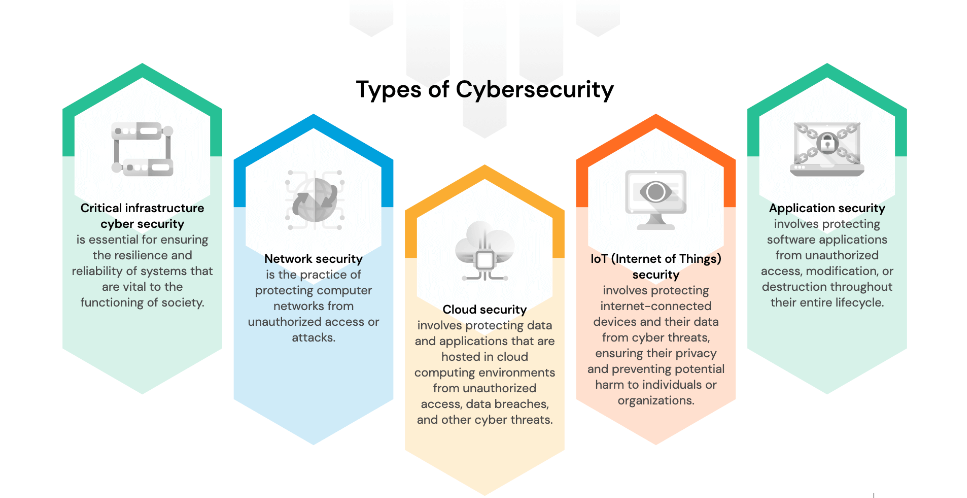
- Network Security
- Endpoint Security
- Cloud Security
- Data Security
- Identity and Access Management (IAM)
- Incident Response and Forensics
Each of these areas is very important for keeping private data safe and stopping people from getting in without permission. Let’s take a closer look at what each cyber security service does to keep us safe from cyber threats.
Common Types of Cyber Security Services
1. Network Security
Network security services are all about keeping an organisation’s network infrastructure safe. This means taking steps to keep network systems and devices safe from hackers, unauthorised access, and other cyber threats. Some of the methods used in network security services are
- Using a firewall to keep an eye on and manage all network traffic coming in and going out.
- IDPS (Intrusion Detection and Prevention Systems) to find and stop bad activities.
- Virtual private networks, or VPNs, let you make safe connections over public networks, which protects the privacy of your data.
2. Endpoint Security
Endpoint security services are meant to keep computers, laptops, smartphones, and tablets safe from cyber threats. As part of these services, security solutions are put in place to protect endpoints from malware, phishing attacks, and other threats. Some important parts of endpoint security services are:
- It is possible to find and get rid of harmful software with antivirus software.
- Endpoint Detection and Response (EDR) to keep an eye on endpoints and act on any suspicious activity that it finds.
- Device encryption protects data stored on devices by stopping unauthorized access.
3. Cloud Security
There are services that can help you keep the data you store in the cloud safe. As more people use cloud computing, it is important to make sure that resources in the cloud are safe.
Encryption, multi-factor authentication, identity management, intrusion detection and prevention systems, and network isolation technology are some of the tools and methods that you need to keep cloud-based resources safe from unauthorized access and disruption. Attackers will have a more difficult time getting in. It is also a good idea to do regular compliance audits to make sure you are following industry standards and laws like the GDPR.
To summarise, some cloud security services are as follows:
- Data encryption protects sensitive information stored in the cloud.
- Access controls are used to manage and monitor user access to cloud-based applications and data.
- Security monitoring and auditing to help detect and respond to security threats in real time.
4. Data security
Data security services keep private information safe from people who shouldn’t have access to it, theft, or manipulation. There are several types of services and things to do for you to keep your data secure. Encryption is one of the most effective ways to protect data, as it converts it into an unreadable format that can only be accessed with the correct decryption key.
Another method is data loss prevention, or DLP.
DLP helps prevent unauthorized access and accidental loss of sensitive data by monitoring and controlling its movement within and outside of an organisation’s network. It can also enforce policies to prevent data leakage through email, USB drives, or other external devices.
The following are some categories of data security services:
- Encryption to code data so that people who aren’t supposed to can’t read it.
- Data Loss Prevention (DLP) to stop sensitive data from being sent without permission.
- Secure data storage practices to make sure that data is kept safe and that only authorised users can get to it.
5. Identity and Access Management (IAM)
Managing user identities and controlling who can access digital resources are very important jobs that IAM services do. These services are meant to make sure that only people who are allowed to can get into an organisation’s data and systems.
Multi-factor authentication can be one example of what IAM services do. Multi-Factor Authentication (MFA) is an effective IAM service that adds an extra layer of security by requiring users to provide multiple forms of identification, such as a password, fingerprint, or security token. This significantly reduces the risk of unauthorised access and strengthens the overall security posture of an organisation’s data and systems.
Not enough security measures is one of the reasons we listed in our post about why hackers might target your business. For this reason, multifactor authentication (MFA) might be a good addition to your online safety.
Along with MFA, here are some other identity and access management cyber security services:
- Multi-Factor Authentication (MFA) makes things safer by requiring more than one way to prove who you are.
- Single Sign-On (SSO) lets users use the same set of credentials to access multiple apps.
- Identity governance is the process of making sure that rules and policies about user access and permissions are followed.
6. Incident Response and Forensics
Incident response and forensic services are essential for responding to and investigating security incidents. For example, if an organisation experiences a data breach, incident response services would be utilised to contain and mitigate the incident, while forensic services would be used to investigate the breach and identify the source of the attack.
These services help organisations understand how the breach occurred, gather evidence for legal purposes, and take necessary actions to prevent future incidents.
Forensic investigation is one example of their services. In a forensic investigation, highly trained professionals use specialised tools and techniques to analyse digital evidence, such as logs, network traffic, and system artefacts.
Other than forensic investigation, other kinds of incident response and forensic cyber security are as follows:
- Incident detection is used to identify potential security breaches and threats.
- Analysis of security incidents to determine their scope and impact.
- Containment and mitigation of security incidents to prevent further damage.
- Recovery of systems and data affected by security incidents.
- Forensic investigation to gather evidence and identify the root cause of security breaches.
How to Choose the Ideal Cyber Security Services
You are now aware of every cyber security service that can assist you in safeguarding the data belonging to your business. How can companies choose the best cyber security service to safeguard their important data when there are so many options available?
In general, you should think about what your business needs before picking the right cyber security services. In short, these six tips will help you pick the best cyber security services.
- Assess Your Needs: Identify your organisation’s specific cyber security requirements, considering factors such as the size of your business, industry regulations, and the sensitivity of your data.
- Evaluate Service Providers: Research and evaluate cyber security service providers based on their expertise, experience, and track record. Consider factors such as certifications, client testimonials, and industry recognition.
- Consider Scalability: Choose cyber security services that can scale with your business as it grows and evolves. Always make sure that the service provider can accommodate your future needs and requirements.
- Standards Compliance: Make sure that the cyber security services your business uses follow the rules and standards that apply to your industry. Keep an eye out for service providers that are certified and follow guidelines like ISO 27001 and the NIST Cybersecurity Framework.
- Cost-effectiveness: Think about how much cyber security services cost in relation to how much value they bring to your business. To make sure it’s affordable, compare different pricing models and figure out the total cost of ownership.
- Support and Maintenance: Choose a service provider that offers reliable support and maintenance services to address any issues or concerns promptly.
Conclusion
Last but not least, safeguarding information systems, networks, and data online from cybercriminals requires cyber security services. Organisations can reduce risks and strengthen their cyber defences by learning about the various types of cyber security services and then using best practices to choose the best ones.
If you’re looking for services to protect your company’s data from cyber threats, look into Nexa Lab security hardening services.
We provide a wide range of cyber security services, including vulnerability assessments, application security enhancements, incident response planning, custom security strategies, access control and authentication, and security awareness training.




