Imagine a situation where cyber criminals attack your small business. Valuable customer data is stolen, your website shuts down, and financial losses pile up.
Sounds devastating, right? Unfortunately, this scenario is more common than you might think. Cyber attacks are on the rise, and small businesses are increasingly becoming targets due to their perceived vulnerability.
But here’s the good news: you don’t have to be a victim! By implementing a cyber security plan, you can reduce your risk of a successful attack and minimise potential damage.
This guide will equip you with the knowledge and tools needed to create a robust cyber security plan for your small business.
Importance of a Cyber Security Plan
Think of a cyber security plan as a protective shield for your business. It outlines the strategies, policies, and procedures you’ll employ to defend against cyber threats. Here’s why having a plan is crucial:
- Proactive approach: Instead of reacting to an attack, your plan empowers you to proactively identify and address vulnerabilities before they can be exploited.
- Reduced risk: Implementing the measures outlined in your plan minimises the likelihood of a successful attack, safeguarding your data, systems, and reputation.
- Minimised damage: Even if an attack occurs, a well-defined plan helps you respond quickly and efficiently, minimising the impact on your business.
- Compliance: Certain industries may have regulations requiring specific cyber security measures. A plan ensures you meet those requirements.
What to Include in Your Cyber Security Plan Template
Creating a comprehensive cyber security plan might seem daunting, but it doesn’t have to be. This guide breaks down the essential components you need to consider:
1. Risk Assessment
The first thing you should do in your cyber security plan template is do a risk assessment. In other words, you need to look for threats and weak spots in your defences that could cause your business harm. Once you know about these risks, you can make your next plan. Because you can’t protect yourself if you don’t know what kinds of IT assets you have, where they are weak, and how risks are ranked.
For example, here are several assets that might be important for your small business:
- Financial data.
- PCs and mobile devices.
- Customer information.
- Cloud-based data.
- Networks and servers.
Think about how to protect those assets first. After you’ve made a list of your assets, you might want to make a to-do list to protect them. You can learn more about this subject in our “Cybersecurity Checklist for Small Businesses“ article.
2. Security Controls and Measures
Security controls and measures to protect are another important aspect to implement for protecting assets from potential threats. Examples of this can include setting up firewalls, antivirus software, encryption, and access controls to safeguard your data and systems. According to the US Federal Communications Commission, regular security audits and updates can help you guarantee that your defences are up-to-date and effective against cyber threats.
Some examples of security controls and measures include:
- Network security: Implement firewalls, intrusion detection systems, and secure network configurations to protect your internal network.
- Endpoint security: Install antivirus, anti-malware, and endpoint detection and response (EDR) solutions on all devices accessing your network.
- Data security: Encrypt sensitive data, implement access controls, and regularly back up your data to safeguard against loss or compromise.
- Password management: Enforce strong password policies, enable multi-factor authentication, and educate employees on secure password practices.
- Security software updates: Regularly update your operating systems, applications, and firmware to patch vulnerabilities.
You can ask your IT team to come up with security measures and controls. You can always hire an IT consultant if your small business doesn’t have its own IT team.
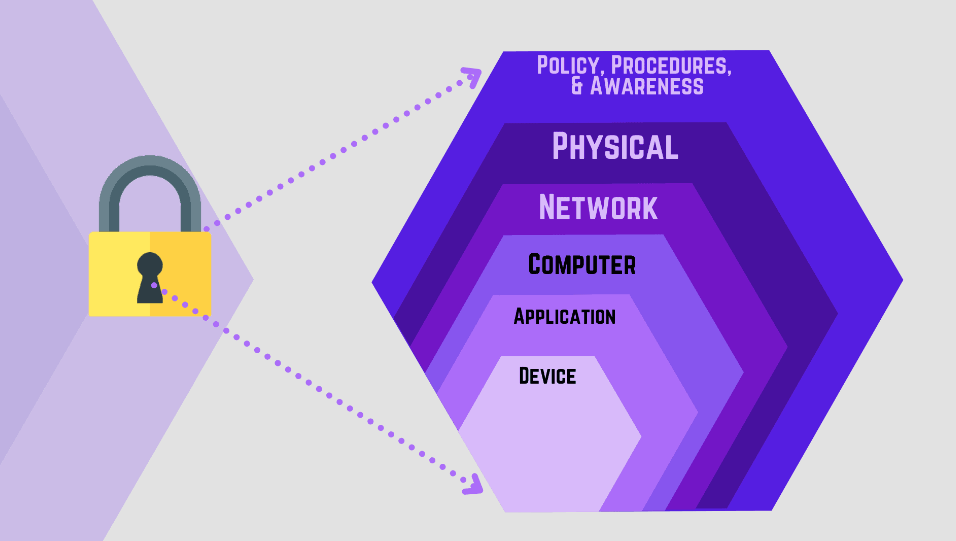
3. Policies and Procedures
The next step in your cyber security plan is to create and clearly define policies and procedures. Your business’s cyber security plan will be useless if you are the only one who knows how to handle the data. Make sure your team understands the plan by implementing policies and procedures.
This includes guidelines on password management, data encryption, and acceptable use of company devices. Regular training sessions can help reinforce these policies and ensure that all employees are aware of their responsibilities in maintaining cyber security.
Here are some examples of cybersecurity policies and procedures.
- Acceptable Use Policy (AUP): Define acceptable and prohibited uses of company technology and data.
- Incident Response Plan: Outline clear steps for identifying, containing, reporting, and remediating cyberattacks.
- Data Breach Notification Policy: Establish procedures for notifying affected individuals and authorities in case of a data breach.
- Physical security: Implement measures to control access to physical devices and sensitive information.
With a clear procedure, you can reduce the possibility of cyberattacks. Check out our other article on “cyber security policies for small businesses“ to learn more about some of the procedures you can apply to your business.
4. Incident Response Plan
All of the plans we laid out above are preemptive measures to protect against cyberattacks. However, cyberattacks can be unavoidable.
So, what should we do when cyberattacks occur? That is why the final component of your cybersecurity plan is to develop an incident response plan. This plan was created to put together a set of instructions on what your company should do when a cyberattack occurs.
Some examples of incident response plans are:
- Detection and reporting: Define how you’ll identify potential attacks and reporting procedures for employees.
- Containment and mitigation: Outline steps to contain the attack, prevent further damage, and minimise data loss.
- Investigation and recovery: Establish procedures for investigating the incident, gathering evidence, and restoring affected systems.
- Communication: Define communication protocols for informing stakeholders about the incident and its resolution.
The incident response plan should be reviewed and updated on a regular basis. Cyber threats are constantly evolving, so your business must adapt accordingly. While this plan appears to be solid, you should still conduct regular training and simulations to be sure that your team is prepared to respond quickly and effectively in the event of a cyberattack.
How to Create and Implement a Cyber Security Plan on Business
You already have a cyber security plan, but what are the steps required to create and implement it? As the saying goes, a plan is only a plan if it is not practiced and implemented. There are at least six steps that you must take to create and implement your cyber security plan, which are:
- Assemble a team: Form a team representing different departments to participate in plan development and implementation.
- Gather resources: Utilise online resources, government guides, and cybersecurity professionals for assistance.
- Tailor the plan: Customise the plan to reflect your specific business needs, industry regulations, and budget constraints.
- Train and educate: Regularly train employees on cyber security best practices and the importance of adhering to your policies.
- Test and revise: Regularly test your plan through simulations and tabletop exercises to identify and address weaknesses.
- Seek professional help: Consider consulting cybersecurity professionals for assistance with more complex aspects of your plan.
Remember, cyber security is an ongoing process, not a one-time event. Do a regular review, update, and implementation of your cyber security plan. With that, you can build a resilient defence against the constantly changing threat landscape.
Conclusion
To wrap up this article, keep in mind that you must always stay up-to-date on cyber security topics. Having a plan is already a step in the right direction for your small business, but keep in mind that cyber security is an ongoing process that must be done daily.
Protecting your company’s data from cyber threats requires a team effort. That’s why, at some point, you may require assistance from professionals, such as Nexa Lab security hardening services.
We provide a wide range of cyber security services, including vulnerability assessments, application security enhancements, incident response planning, custom security strategies, access control and authentication, and security awareness training.
Nexa Lab was founded and established in Australia, with over 30 years of experience in the MSP and IT industries. With a commitment to cybersecurity, we prioritise protecting Australian businesses’ digital assets and sensitive data.




